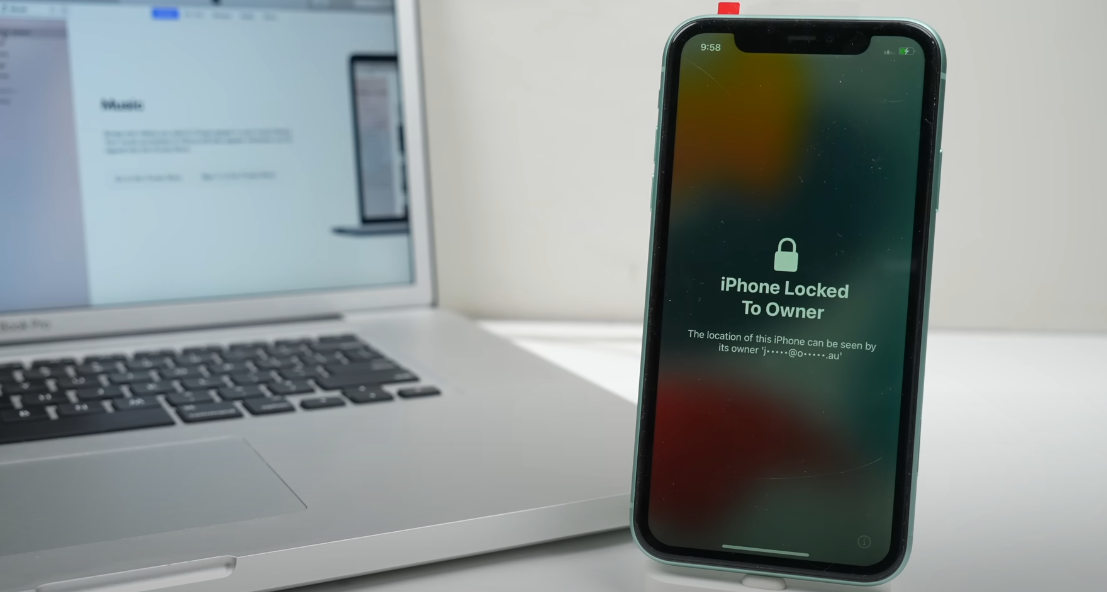
In the world of digital security, even the most trusted brands can sometimes have vulnerabilities lurking beneath the surface. Apple, a company renowned for its stringent security measures, has a hidden flaw in its iCloud system that could potentially allow someone to remotely lock your device—without ever needing physical access to it. This security breach is tied to an unpatchable exploit that exploits a weakness known as Checkmate.
The Checkmate Exploit: An Inescapable Vulnerability
The Checkmate exploit, which surfaced a few years ago, targets a critical part of Apple’s security system: the boot ROM. The boot ROM is a read-only memory chip that stores crucial code to initialize the device when powered on. Because this code is stored in read-only memory, it cannot be patched through a software update, leaving older Apple devices vulnerable to exploitation.
The exploit affects older models up to the iPhone 10, iPad 7, iPad Mini 4, iPad Pro second generation, and the iPod Touch 7. Though it requires physical access to the device to exploit, the danger lies in how Apple’s activation servers interact with serial numbers and device identities.
How the Vulnerability Works: A Remote Attack
Here’s where things get particularly concerning: the Checkmate exploit doesn’t require physical access to your device to cause significant disruption. By swapping serial numbers, Wi-Fi addresses, and Bluetooth addresses between devices—an act made possible by the vast availability of serial numbers for sale on websites like AliExpress—someone can essentially “clone” the identity of your device.

Once the serial number from one device is copied and transferred to another, Apple’s activation servers may mistakenly believe that the device with the new serial number is the same as the original, granting it access to activation services. However, there’s a significant catch: the serial number being used may not come from a device you own. In fact, it may have been stolen from someone else’s device, leaving you powerless to retrieve it.
This process can cause your device to become “locked” under someone else’s Apple ID, effectively locking you out of your own device. And the situation becomes even worse if the serial number belongs to a device that’s already activation locked. This phenomenon has already led to people purchasing brand new, sealed devices, only to find them locked to someone else’s Apple ID—unusable out of the box.
The Impact: From Stolen Devices to E-Waste
This flaw within Apple’s activation lock system can lead to significant issues beyond just individual inconvenience. For one, the entire concept of activation lock, designed to secure lost or stolen devices, becomes a double-edged sword. If your device is locked to someone else’s Apple ID, even if you have proof of purchase, Apple may refuse to unlock it for you. The policy is clear: the device will only be unlocked for its original owner with proof of purchase, but even then, if the device is marked as “lost” or “stolen,” you’ll find no help.
The result is a growing problem of e-waste. Devices that could otherwise be repurposed or repaired are being rendered useless because of a flaw in Apple’s system. This also drives up the demand for new devices, contributing to both environmental damage and a culture of forced obsolescence.
How to Protect Yourself
Given the risks associated with iCloud’s activation lock vulnerability, you may be wondering how to protect yourself. While Apple’s activation lock system offers some security, the easiest way to safeguard your devices is by ensuring that Find My iPhone (or Find My device) is enabled on your account. This enables you to track your devices remotely and makes it more difficult for someone to lock your device without your permission.
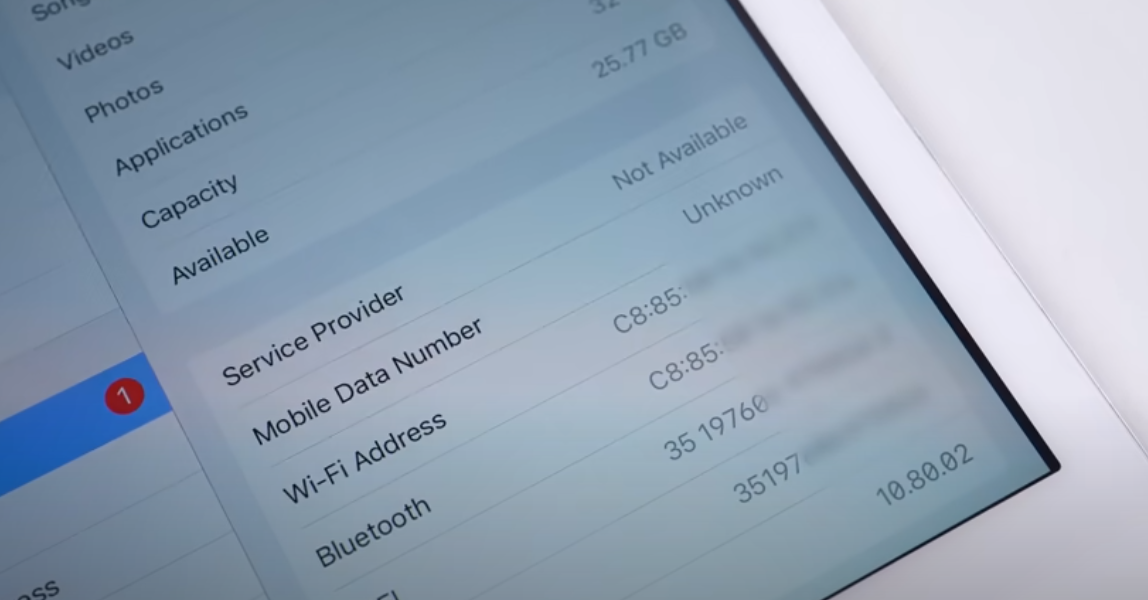
It’s also essential to protect your serial number and device details when selling your old device online. Avoid posting pictures of your device’s serial number, Wi-Fi address, or Bluetooth address on social media or e-commerce platforms, as these can be used by malicious individuals to exploit the system. If you’re selling your device, consider wiping it thoroughly and factory resetting it, as well as transferring ownership through Apple’s official channels.
A Glimpse into the Future: Could Apple Fix This?
One of the key solutions would be for Apple to improve their activation lock system, so that it doesn’t lock devices that are not marked as lost or stolen. With an enhanced system in place, even if someone tries to bypass it by changing serial numbers, it would become much harder to lock a device that isn’t truly stolen. Unfortunately, as of now, Apple has not yet addressed this flaw in a way that would prevent the abuse of serial number swaps.
Until that happens, however, it’s crucial to take steps to protect your device and its unique identifiers. This includes ensuring that your Apple ID and iCloud account are secure and active, as well as remaining vigilant about who has access to your serial number.
Conclusion: Navigating the Flaw in Apple’s System
While Apple’s security measures are generally robust, this overlooked flaw in the iCloud activation lock system poses a risk that cannot be ignored. The potential for someone to lock your device remotely, simply by exploiting serial numbers and device information, is a growing concern. However, with the right precautions—such as using Find My and protecting your device’s serial number—you can minimize the chances of becoming a victim.
As the digital landscape continues to evolve, it remains to be seen whether Apple will take meaningful steps to address this flaw. Until then, we must remain vigilant and proactive in securing our devices from those who seek to exploit vulnerabilities in the system.



